A common myth associated with remote desktops is that security can be compromised. However, with the proper setup and protocols, these systems can be secure when protecting your data from cyber-attacks. This article will explore how to set up a secure desktop environment for remote work and provide some tips for first-time users.
The most important factor for establishing a secure desktop environment starts with the right hardware and software configuration. Ensure that all devices have updated operating systems and applications to reduce vulnerabilities. Additionally, deploy other protective measures such as firewalls and anti-virus protection software to protect against malicious intrusions.
Introduction to Remote Desktops
Let's begin with understanding what remote desktops are and how they can be used to boost productivity. Remote desktops, sometimes called virtual machines, allow users to access their work environment from any location while maintaining the same level of security as if they were in the office. This is possible because all data and applications are stored off-site on a secure server. It is possible to further secure this data by encrypting it so that even if a hacker gained access, it would be impossible for them to use the information.
Remote Desktop Protocols
The next step is to establish protocols for using your remote desktop. These protocols include setting up user authentication and authorization methods, such as assigning passwords or access tokens, to ensure that only authorized users can access the system. Additionally, it is important to keep a log of all activity to quickly identify and address any suspicious behavior. To further protect against cyber-attacks, set up rules for the acceptable use of company resources when using remote desktops.
Support Requirements
Considering support requirements for secure desktop environments with multiple users is also important. Most organizations will need some level of technical support to troubleshoot any issues experienced with the systems or applications being used on their secure desktops. If a company does not have the internal resources to support its users, it is best to outsource this need.
Access Policies
Finally, create access policies that specify which users can access certain systems and applications from remote desktops. Access policies ensure that only the people authorized to use a particular system or application can access it. Additionally, companies should consider creating policies around data storage and maintenance of user accounts on their secure desktop environment.
Enhance Productivity and Security
By setting up secure desktop environments for remote work, businesses can ensure that their data is safe from cyber-attacks while still providing a way for employees to access the systems they need to be productive. Additionally, with the right protocols and support requirements in place, companies can rest assured that their users can work securely on their secure desktops. With these best practices, organizations can enhance productivity while protecting valuable corporate information.
Eliminate Security Breaches
By following these steps and best practices, organizations can help prevent security breaches due to unsecured desktops. When it comes to protecting your data, a secure desktop environment is the best way to go. With proper planning and the right protocols, businesses can rest assured that their remote work environments are safe from cyber-attacks.
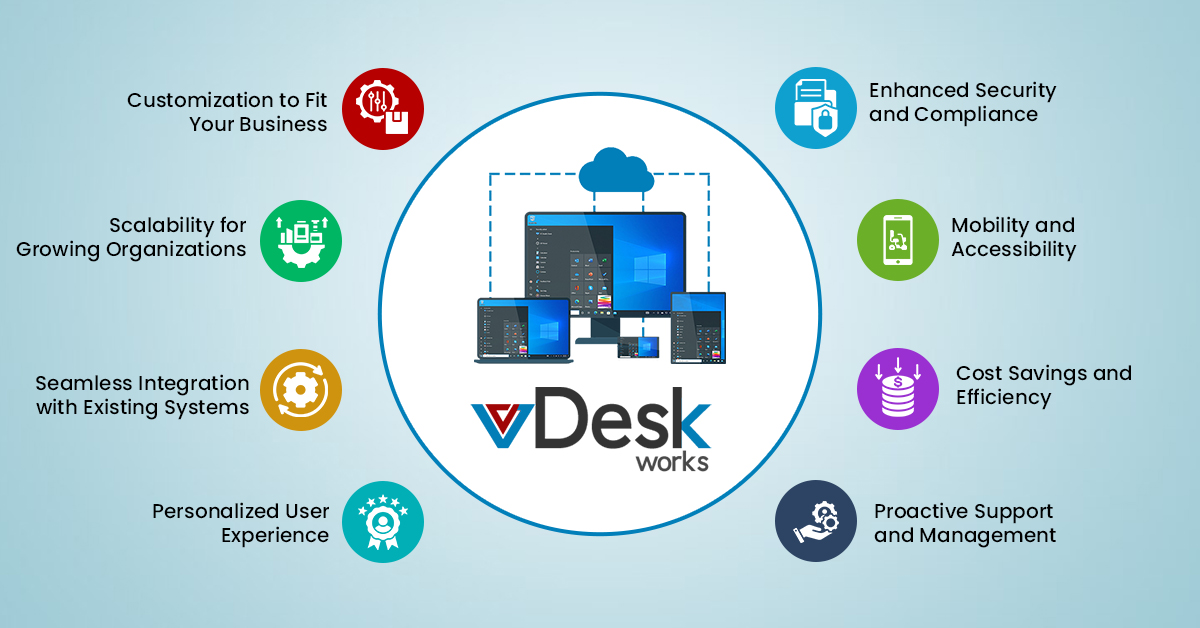
vDesk.works: A Secure Desktop Environment Solution
vDesk.works is a secure desktop environment solution for businesses of any size. Our cloud-based desktop hosting solutions provide organizations with a secure and easy-to-use platform for remote users.
With our complete security package, you can rest assured that all data and applications are protected from malicious intrusions and unauthorized access while allowing employees to work securely from anywhere in the world. Contact us today to learn more about how vDesk.works can help your organization be more productive while maintaining the highest level of security.
Secure desktop environments are essential to protecting your data and ensuring the safety of your remote users. By following these best practices, businesses can ensure that their remote work environment is as safe and secure as possible while enabling employees to be productive. With a comprehensive solution like vDesk.works, organizations can protect their valuable information and enhance user productivity simultaneously.
To start establishing your secure desktop environment today, contact us to learn more about our cloud-based solution. We look forward to helping you take the next step in protecting your data!


 Lauren King
Lauren King